
The Role of DevOps in Building Robust Web3 Infrastructure
Photo by [Annie Spratt](https://unsplash.com/@anniespratt?utm_source=unsplash&utm_medium=referral&utm_content=creditCopyText) on …

Why Endpoint Security is Crucial in a DevOps Environment
Photo by [Christopher Gower](https://unsplash.com/@cgower?utm_source=unsplash&utm_medium=referral&utm_content=creditCopyText) on …

15 App Categories to Explore as a Smartphone Owner
Photo by [Greta Hoffman](https://www.pexels.com/photo/unrecognizable-man-browsing-smartphone-on-bed-7674820/) Smartphones are the modern-day …

Ultimate Guide to Deploying a Jenkins Multinode Cluster on AWS with Linux and Windows Slave Nodes
Jenkins is an open-source automation server that helps automate parts of the software development process, including building, testing, and deploying …
How to Use Bandit to Scan Your Python Code for Security Vulnerabilities
As software developers, we all want to write code that is both functional and secure. However, writing secure code can be challenging, especially if …

Secure Your Containers: Trivy Vulnerability Scanning
https://www.youtube.com/@techinik-devops In today’s digital age, software applications and systems are vulnerable to a wide range of security threats. …
Top 10 Kubernetes Monitoring Tools for 2023
Kubernetes is a powerful container orchestration system that can help you manage your applications and services with ease. However, monitoring your …
Customizing Ansible: Ansible Module Creation
Ansible: is an open-source software for configuration management, provisioning and application deployment, it comes under the Infrastructure as a …
Decision Systems/Rule Base + Event-Driven Ansible
We use a rule base to find the new routing path with the lowest cost. RHDM gives the path from J to k. Kafka event is the communication channel for …

How to Keep Your Google Cloud Account Secure
Photo by [Obi Onyeador](https://www.pexels.com/photo/grayscale-photo-of-a-usb-13175225/) With the technology boom, almost everyone around the globe …
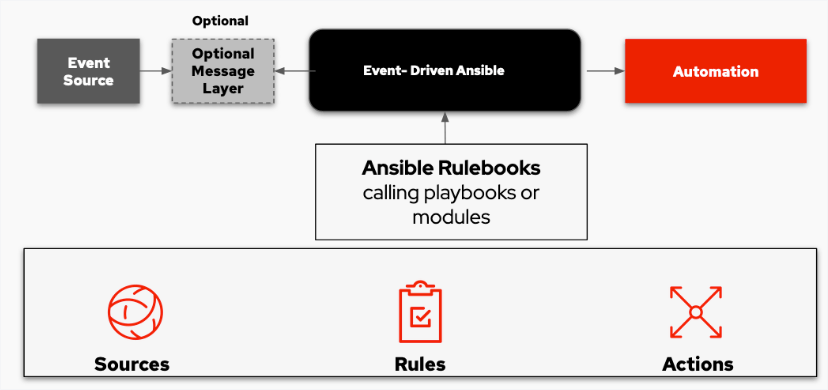
Introducing the Event-Driven Ansible & Demo
In AnsibleFest 2022, Red Hat announced an exciting new developer preview for Event-Driven Ansible. Event-Driven Ansible is a new way to enhance and …
