Configure Red Hat Satellite Content Host with Remote Execution
-
 Gineesh Madapparambath
Gineesh Madapparambath
- Automation, Dev ops, Infrastructre & hardware
- November 5, 2021
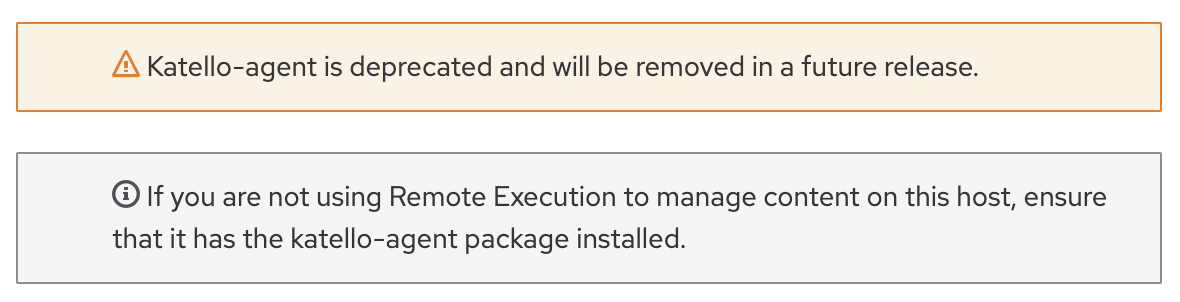
Using Red Hat Satellite is a great way to manage your RHEL servers and contents including updating, patching or installing software packages. A new method for remote content management was introduced with Satellite 6.2 which is called Remote Execution . (katello-agent is deprecated and you will see message like below).
Read Getting started with Red Hat Satellite remote execution .
Distributing SSH Keys for Remote Execution
Satellite Server or Capsule need to access the remote host to perform Remote Execution jobs and this access can be implemented using SSH key based authentication. You have different methods to distribute ssh keys to remote hosts. (You can also manually copy the public content to ~/.ssh/authorized_keys on target system if neither methods are working).
Distribute SSH keys using the Satellite API
Create ~/.ssh directory if does not exist and copy the public key from Satellite server API as show below.
Download the SSH key from Satellite/Capsule
[root@RHEL8-Generic-1 ~]# curl https://satvm.lab.local:9090/ssh/pubkey >> ~/.ssh/authorized_keys
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 411 100 411 0 0 2065 0 --:--:-- --:--:-- --:--:-- 2075
Configure permissions for the ~/.ssh directory:
# chmod 700 ~/.ssh
Configure permissions for the authorized_keys file:
# chmod 600 ~/.ssh/authorized_keys
Configure permissions for the ~/.ssh directory and authorized_keys file.
[root@RHEL8-Generic-1 ~]# chmod 700 ~/.ssh
[root@RHEL8-Generic-1 ~]# chmod 600 ~/.ssh/authorized_keys
Distributing SSH keys to remote hosts manually
If the API method is not working for you, then from Satellite server, use ssh-copy-id command to copy the public key ~foreman-proxy/.ssh/id_rsa_foreman_proxy.pub to remote content host.
# ssh-copy-id -i ~foreman-proxy/.ssh/id_rsa_foreman_proxy root@RHEL8-Generic-1
Verify Satellite/Capsule to Remote Host access using SSH Key
Once you have deployed the ssh key to remote host, verify the password-less access from Satellite or Capsule server.
[root@satvm ~]# ssh -i ~foreman-proxy/.ssh/id_rsa_foreman_proxy root@RHEL8-Generic-1
Last login: Fri Nov 5 05:35:08 2021 from 192.168.1.69
[root@RHEL8-Generic-1 ~]#
Run a Test Job to verify Remote Execution
Goto Monitor -> Jobs -> Run Job
Apply appropriate filter to select the hostname and submit job. (You can use any commands to test like uptime , date or some simple commands.)
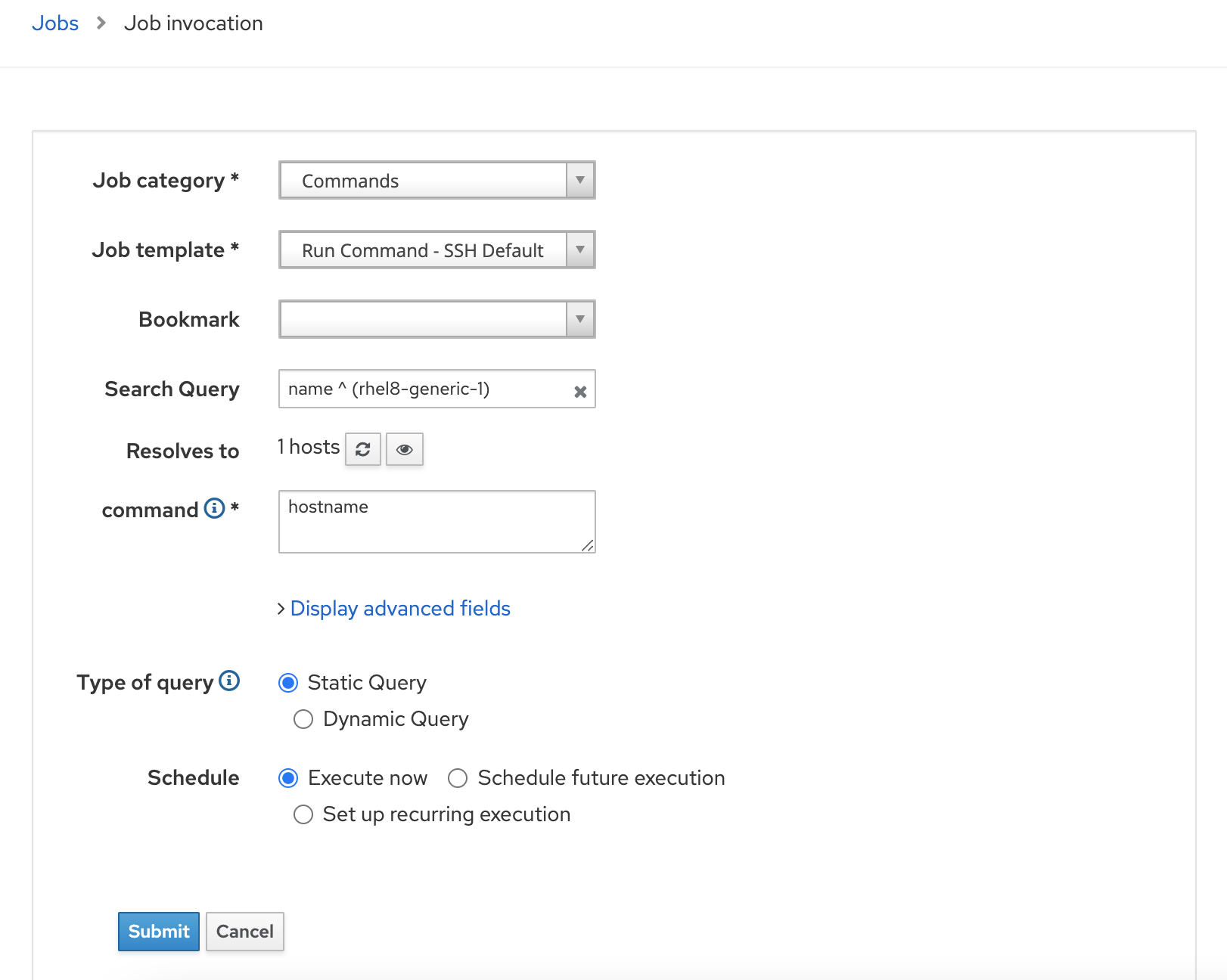
You will see details of jobs in next screen as below.
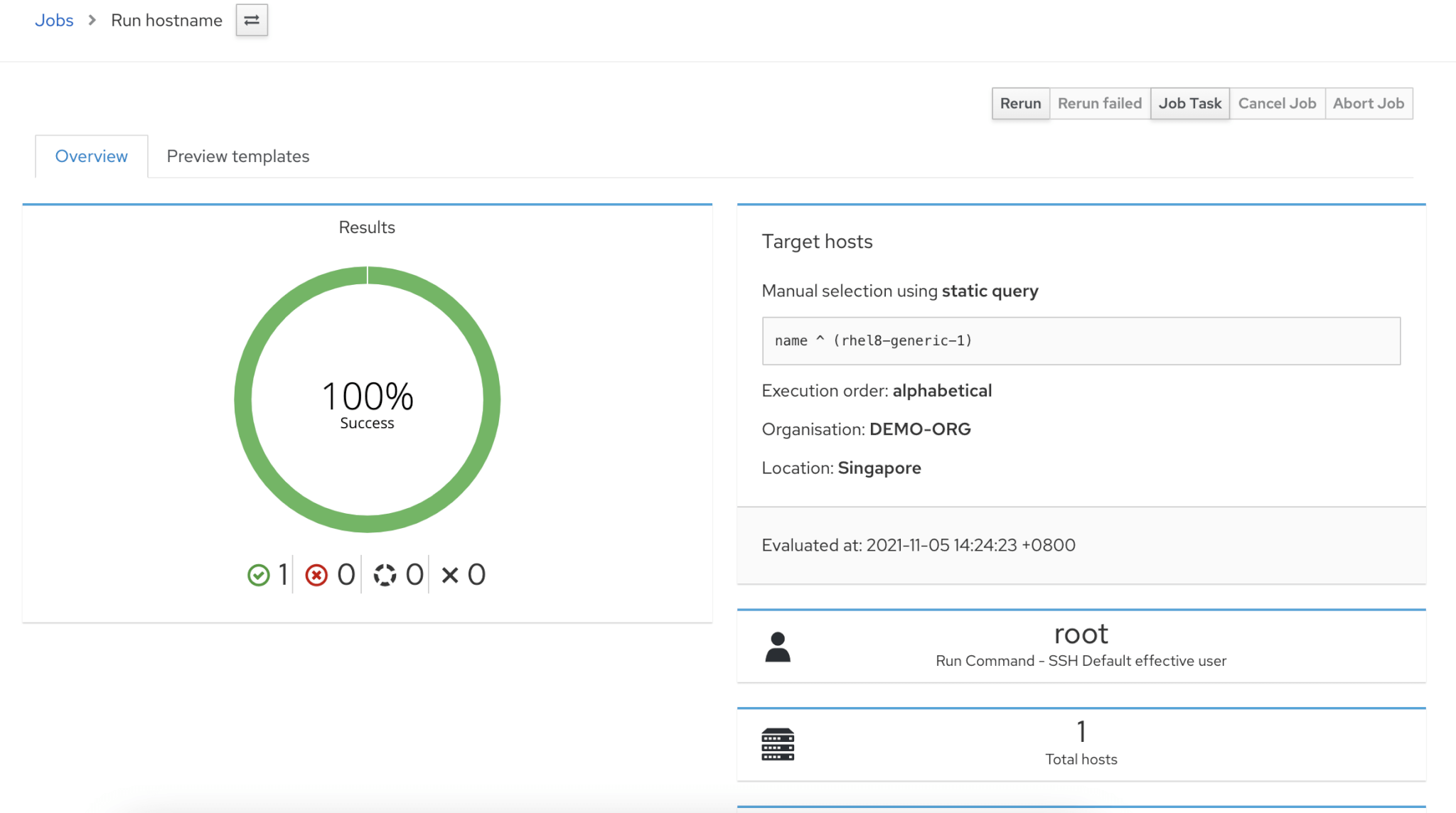
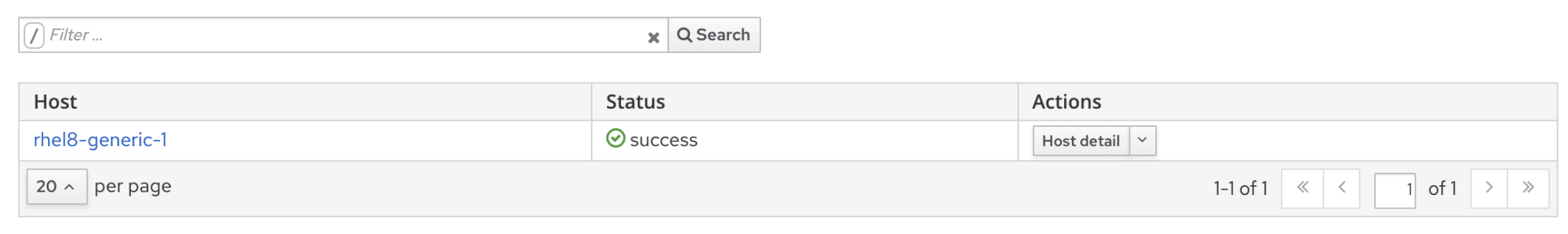
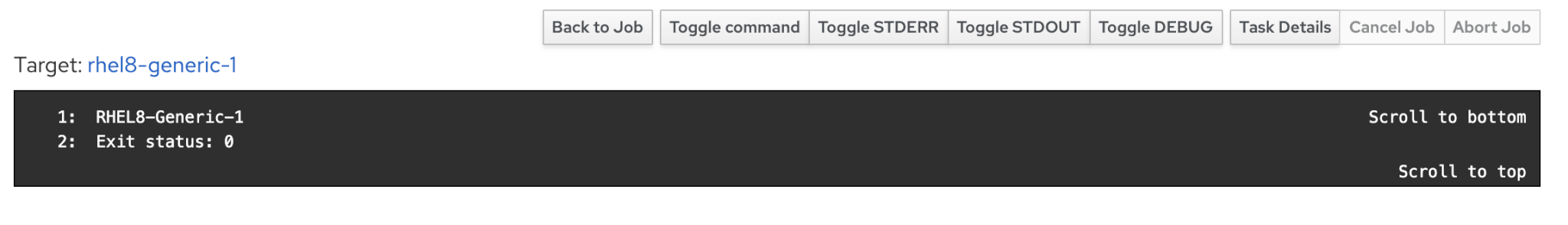
If you want to see details of job, then scroll down and select the host to find job output.
Installing Package or Erratas using Remote Execution
Once you have implemented the Remote Execution for content hosts, you can install packages and updates from Satellite GUI without login to individual hosts.
Installing Package using Remote Execution
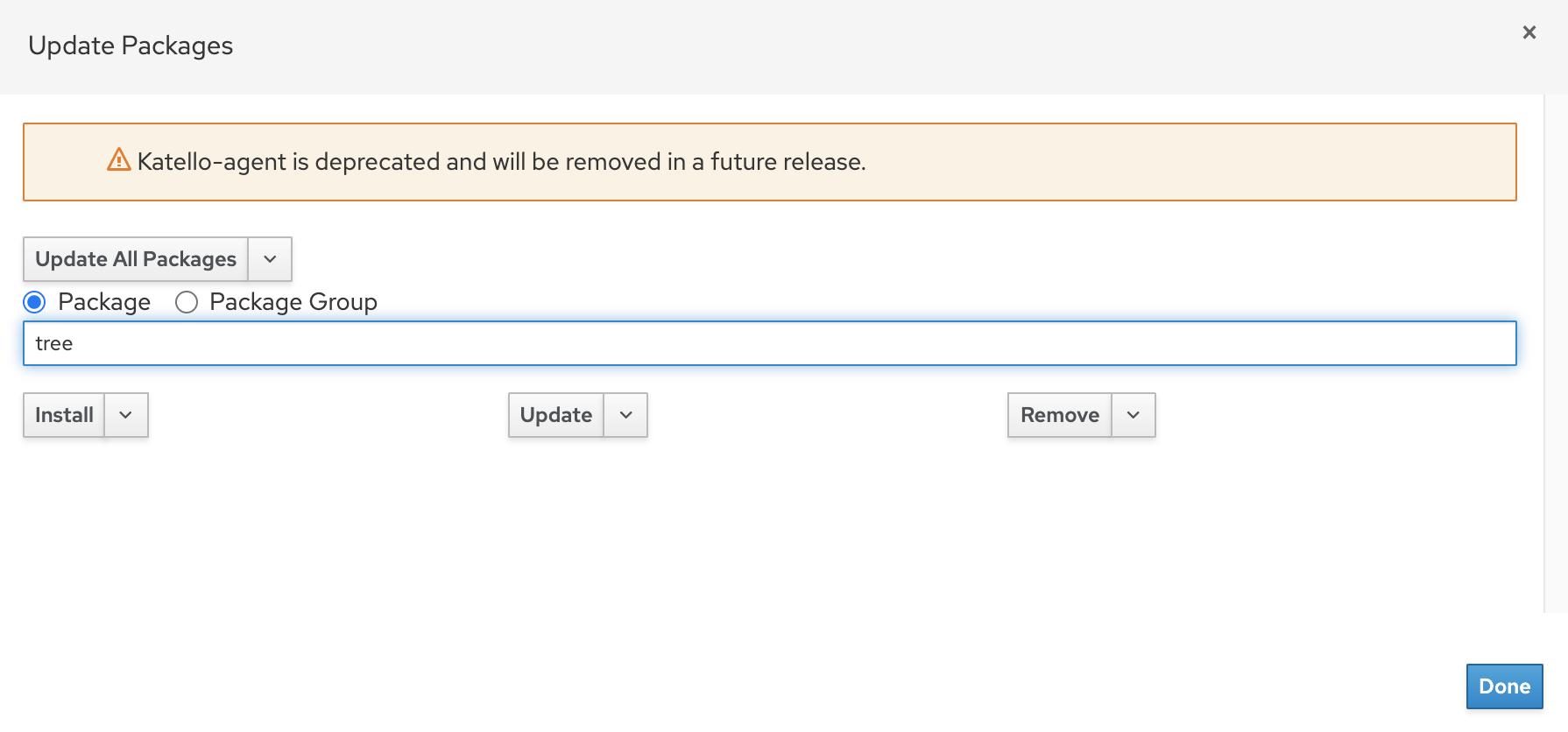
Hosts -> Content Hosts -> Select the hosts and select Manage Packages from Action menu.
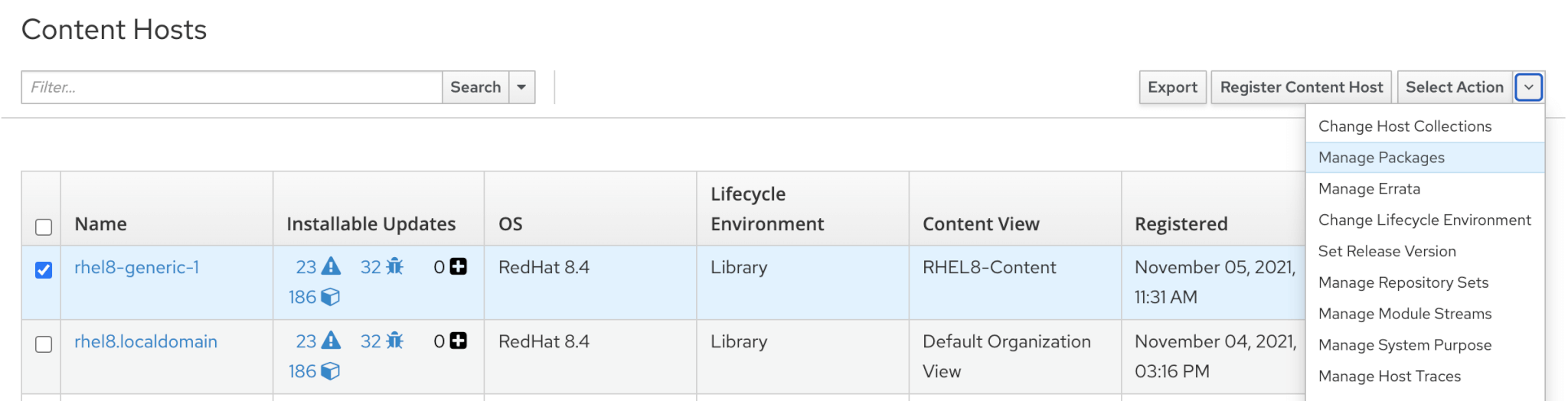
Enter the package details and select and action (Install/Update/Remove)using Remote Execution.
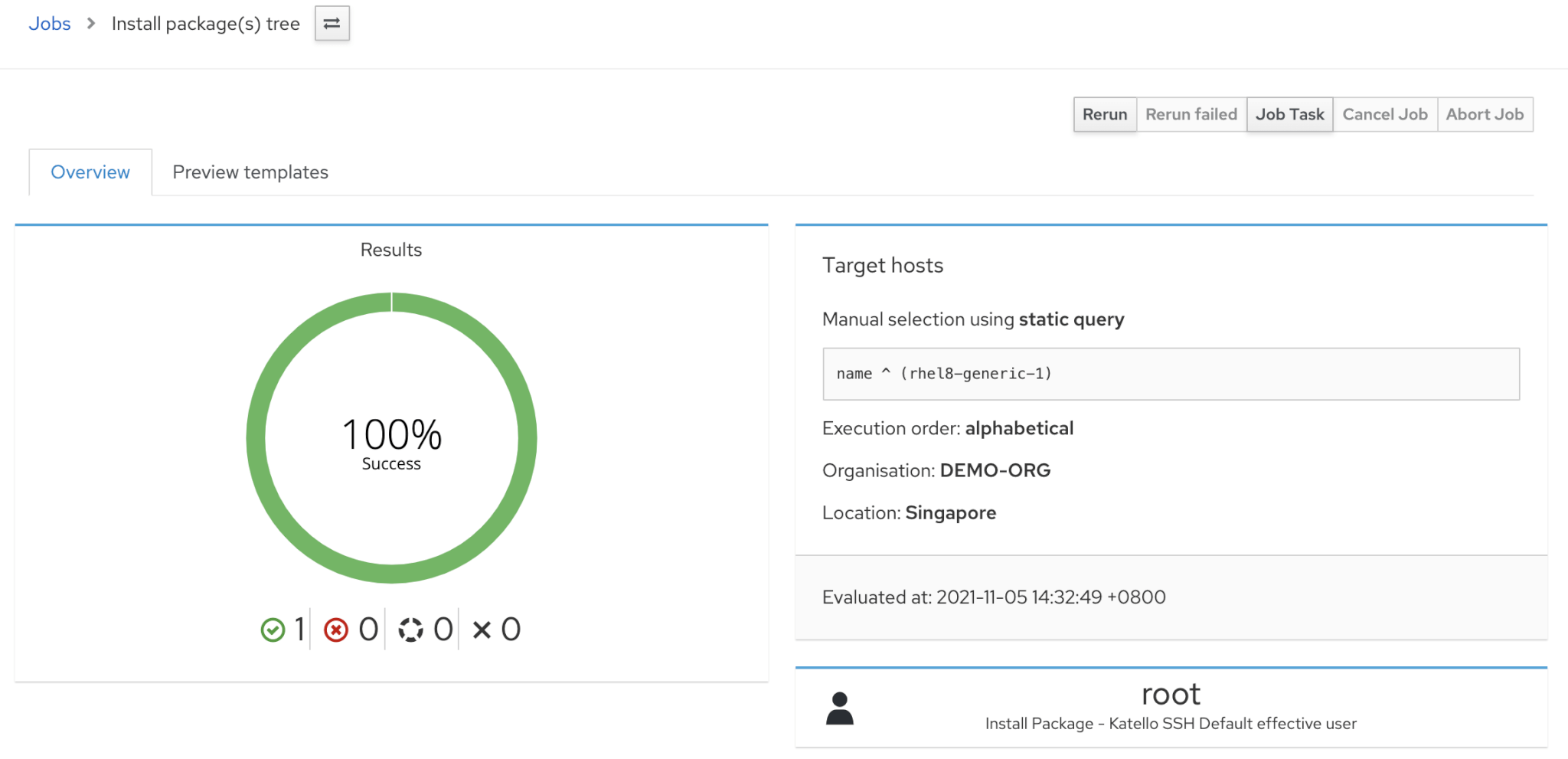
You will see the job details in next screen.
Verify the package installation on remote host
[root@RHEL8-Generic-1 ~]# yum list installed tree
Updating Subscription Management repositories.
Installed Packages
tree.x86_64 1.7.0-15.el8 @rhel-8-for-x86_64-baseos-rpms
Installing Erratas using Remote Execution
Follow the same steps as previous but select Manage Erratas . In the pop-up screen, select required erratas or Select ALL xx option.
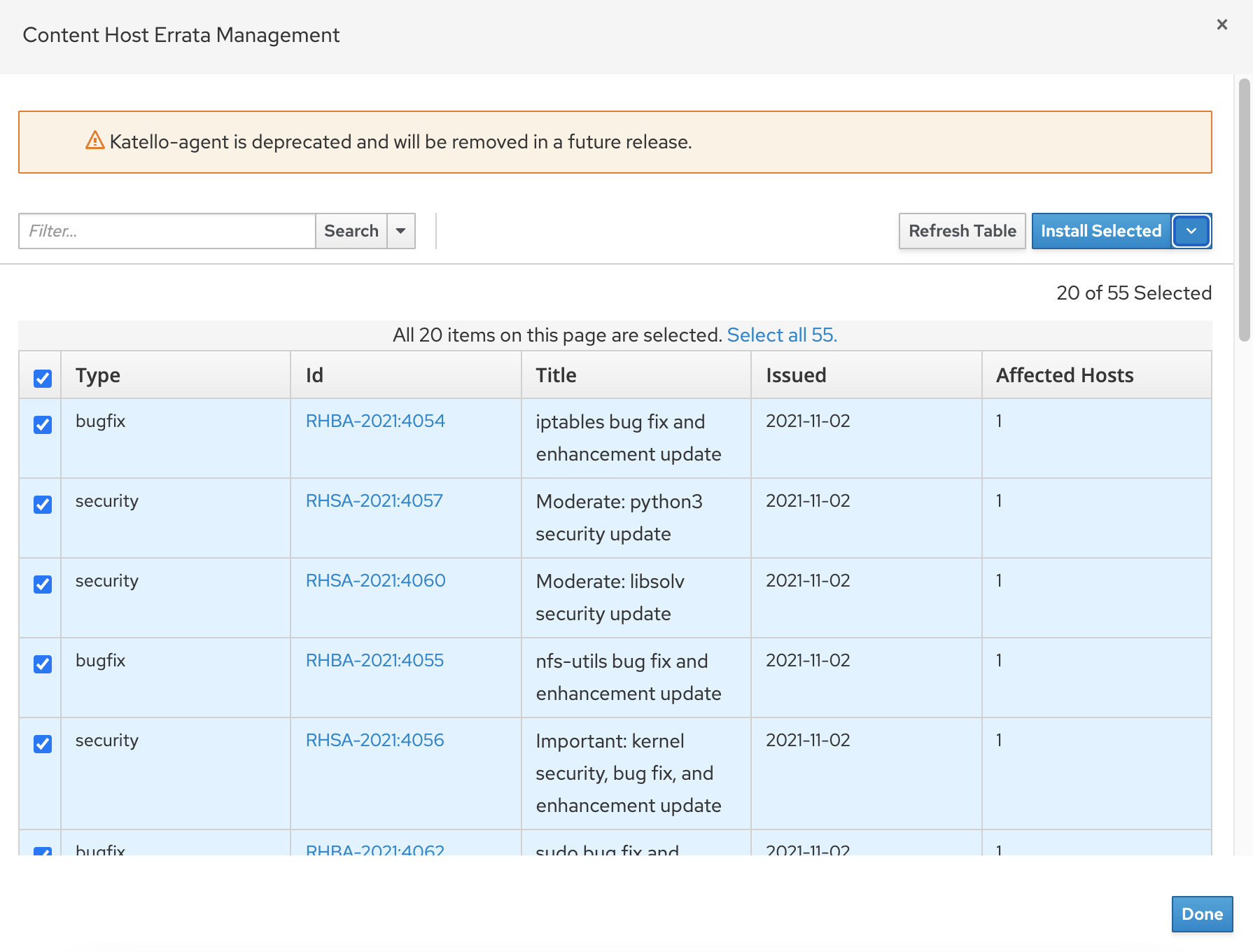
Then click Install Selected -> via remote execution
Wait for the job to be completed and verify on remote host as well. You can monitor the job anytime from the Monitor -> Jobs screen.
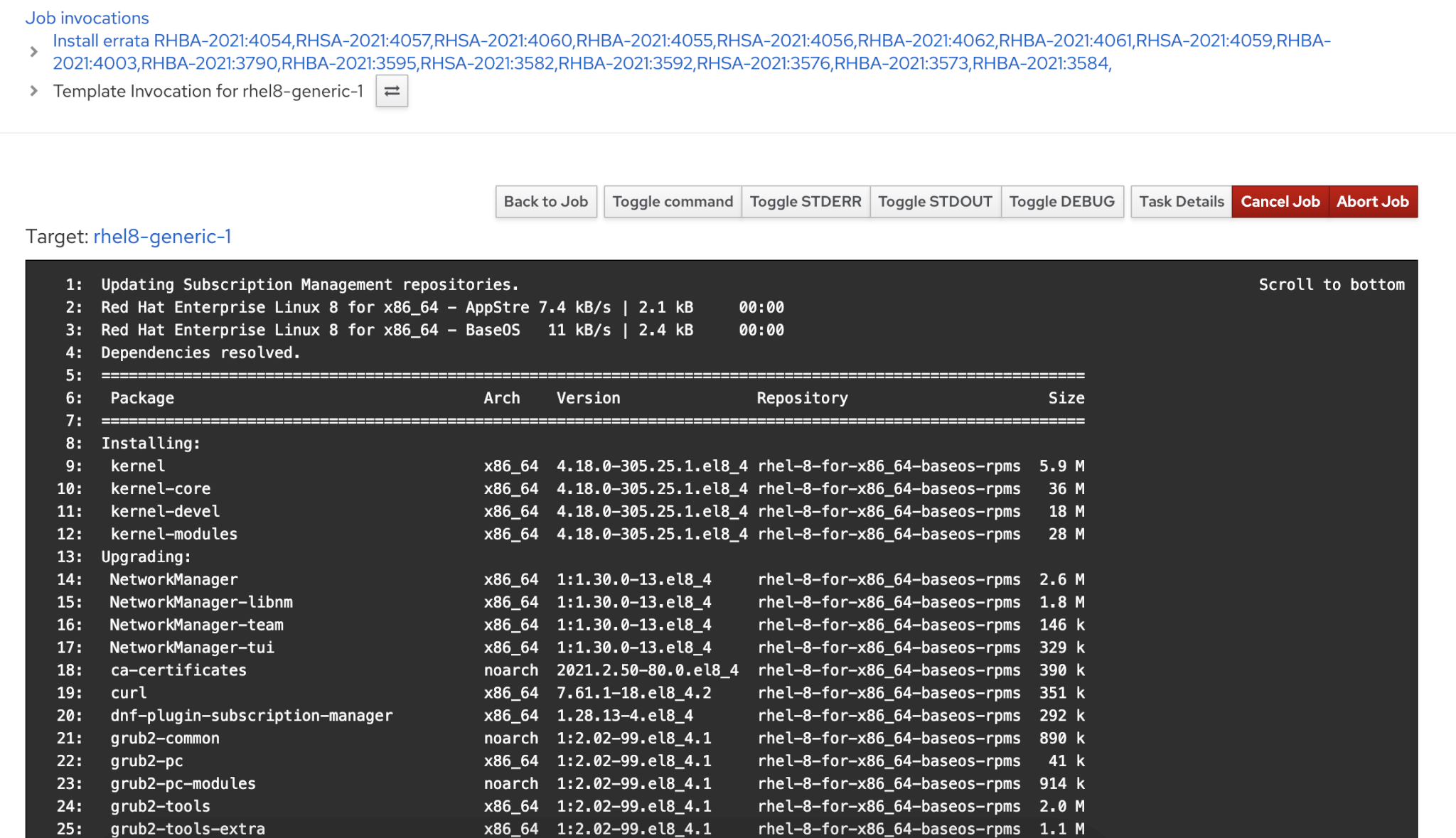
You can see the logs without login to individual remote hosts which will be more easy compared to standard manual method of installation or upgrade.

Read Red Hat Satellite – Managing Hosts official documentation.
See all of our Red Hat Satellite guides to learn more.

Gineesh Madapparambath
Gineesh Madapparambath is the founder of techbeatly. He is the co-author of The Kubernetes Bible, Second Edition and the author of Ansible for Real Life Automation. He has worked as a Systems Engineer, Automation Specialist, and content author. His primary focus is on Ansible Automation, Containerisation (OpenShift & Kubernetes), and Infrastructure as Code (Terraform). (Read more: iamgini.com)
Note
Disclaimer: The views expressed and the content shared in all published articles on this website are solely those of the respective authors, and they do not necessarily reflect the views of the author’s employer or the techbeatly platform. We strive to ensure the accuracy and validity of the content published on our website. However, we cannot guarantee the absolute correctness or completeness of the information provided. It is the responsibility of the readers and users of this website to verify the accuracy and appropriateness of any information or opinions expressed within the articles. If you come across any content that you believe to be incorrect or invalid, please contact us immediately so that we can address the issue promptly.