Red Hat OpenShift Compliance Operator – Overview
-
 Anand Vyas
Anand Vyas
- Cyber security, Kubernetes, Open shift
- April 11, 2023

Overview
Growth in digital services and faster time to market by various global and government organisations, Security has become one of the important aspect of any platform that runs sensitive or regulatory workloads. IT systems are often vulnerable targets from various attackers to steal confidential and user information. In order to protect their systems, organisations adopt industry standards to baseline security and resilience of their IT infrastructure platforms. Many governments have defined their own standards to protect their IT infrastructure from such attacks. Red Hat OpenShift container platform provides secure and scalable platform that enterprises can use to deploy their applications to production along with the required compliance and regulatory requirements. Compliance Operator provides assessment and remediation for various industry and government standards. It performs assessment for OpenShift/Kubernetes API and also the nodes part of the cluster. It uses OpenSCAP under the hood to perform the assessment and remediation. It can be installed on Red Hat OpenShift platform via the Operator Hub.
Profiles
Red Hat OpenShift Compliance operator comes with various industry and government standard profiles. These profiles have different rules of assessment based on the nature of their compliance. Each profile has a prefix in the name that represents the type of compliance rules it is associated with. For example, profile ocp4-cis is for centre for internet security and ocp4-pci-dss is for payment card industry data security standard. As of OpenShift 4.12, list of profiles supported by compliance operator are listed here . After the compliance operator has been installed on the OpenShift cluster, you can run the command oc get profiles -n openshift-compliance to list all the profiles available on the cluster.
Scans
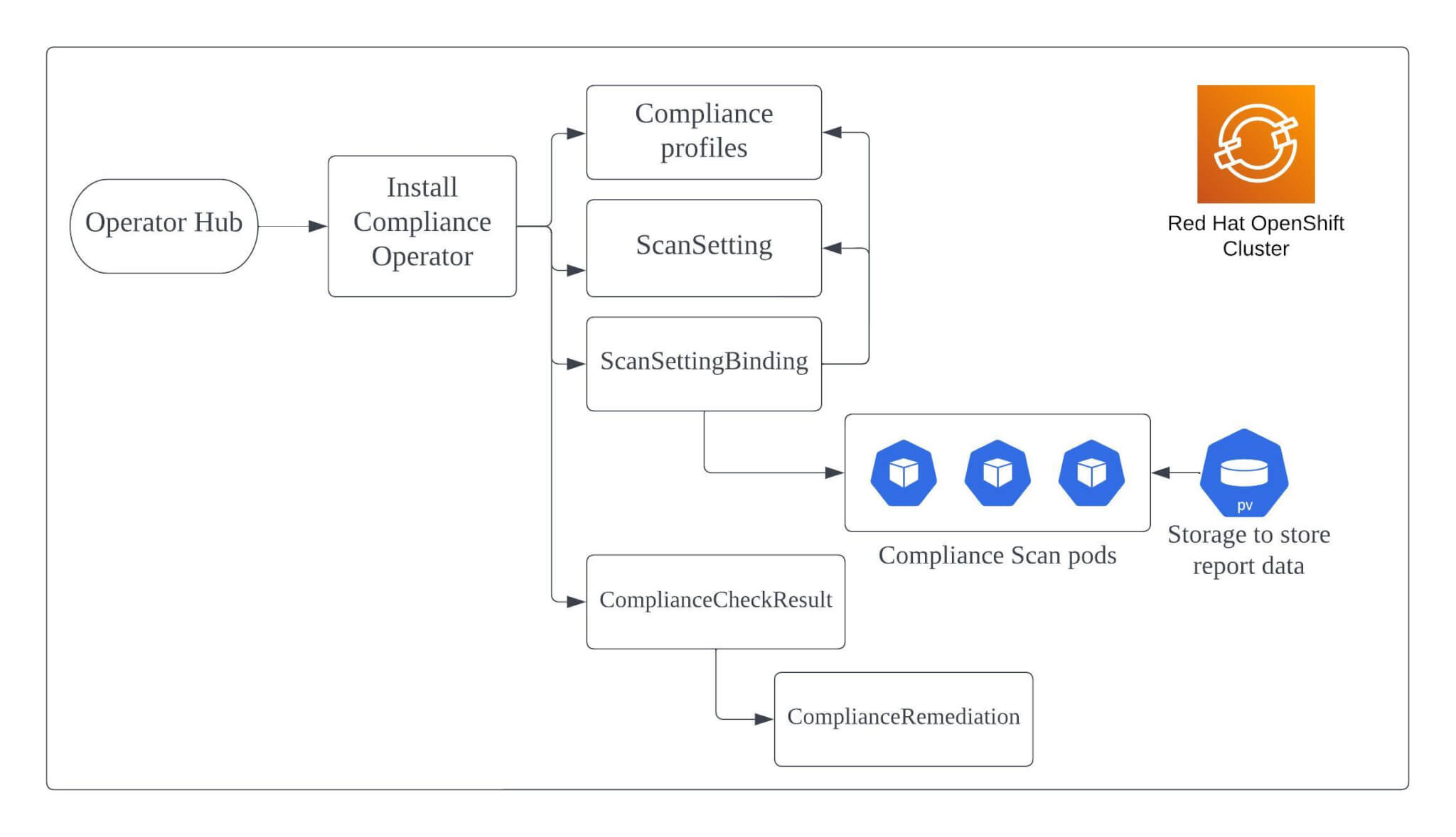
In order to trigger and run a compliance scan on the OpenShift cluster, two custom objects scansetting and scansettingbinding has to be created. These object types are installed as part of the compliance operator installation.
Scansetting object role is to define the necessary schedule of the scans, storage required for the scan results and the subsequent scans you wish to store.
Scansettingbinding object role is to bind the schedule created by the scansetting object with that of a compliance profile, example ocp4-cis . Once scansettingbinding object is created, a compliance scan is triggered and pods are scheduled on the cluster nodes, depending upon the compliance profile and the results are saved on the persistent volume.
Results and Remediations
Once the scan is completed, compliance operator creates compliancecheckresults object for every compliance rule executed part of the compliance profile. Check the status of these rules and based on which further action needs to be taken to remediate the failed assessments.
If the compliance rule has an automated remediation, then an complianceremediation object with the same name as compliancecheckresult is created. Administrator can apply the automated remediation, to update the cluster configuration. If not, then administrators have to apply the remediation manually.
Compliance Operator Flow
Simple flow of the compliance operator that we discussed above.
Conclusion
In this post we discussed overview about how the Red Hat OpenShift compliance operator works. In the future posts we will discuss more in detail about the installation methods, scans, compliance checks and results.

Anand Vyas
Platform Consultant - OpenShift/Kubernetes
Note
Disclaimer: The views expressed and the content shared in all published articles on this website are solely those of the respective authors, and they do not necessarily reflect the views of the author’s employer or the techbeatly platform. We strive to ensure the accuracy and validity of the content published on our website. However, we cannot guarantee the absolute correctness or completeness of the information provided. It is the responsibility of the readers and users of this website to verify the accuracy and appropriateness of any information or opinions expressed within the articles. If you come across any content that you believe to be incorrect or invalid, please contact us immediately so that we can address the issue promptly.