
Implementing Immutable ConfigMaps in Kubernetes: A Practical Tutorial
In this blog post, we will delve into the concept of Immutable ConfigMaps, explore their benefits, and provide practical examples […]

In this blog post, we will delve into the concept of Immutable ConfigMaps, explore their benefits, and provide practical examples […]

While ChatGPT is a powerful language model that can understand and generate natural language, it is not a perfect fit […]

As software developers, we all want to write code that is both functional and secure. However, writing secure code can […]
In today’s digital age, software applications and systems are vulnerable to a wide range of security threats. These threats can […]

No matter the type of tech you are using, protecting your data is critical to the success of any organization. […]

Photo by Desola Lanre-Ologun on Unsplash Introduction In this age of rapidly evolving platforms and applications, user administration has become a complex task. […]

Objective Becoming organization/private PKI provider Shared rootCA certificate to be trusted by client. Creating a Root Certificate Authority 1. Create […]
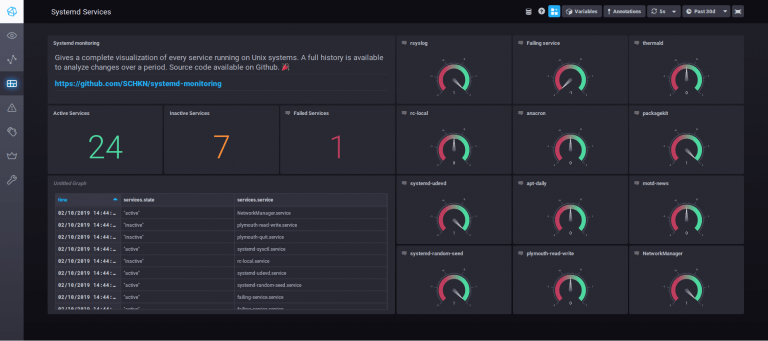
You might be a Sysadmin, developer, DBA or whatever, logs are like treasure boxes for anyone working in IT. And […]
You are browsing some sites or testing your own web applications, and suddenly you receive a white screen with some […]