Secure Your Containers: Trivy Vulnerability Scanning
In today’s digital age, software applications and systems are vulnerable to a wide range of security threats. These threats can […]

In today’s digital age, software applications and systems are vulnerable to a wide range of security threats. These threats can […]

Kubernetes is a powerful container orchestration system that can help you manage your applications and services with ease. However, monitoring […]
Ansible: is an open-source software for configuration management, provisioning and application deployment, it comes under the Infrastructure as a code, which […]

Learn tips and tricks to set up and use Kubernetes Logging to collect logs from all your applications and services […]
This blog demonstrates how to use RHACM GitOps to manage the MySQL application in the development and Production environment. MySQL […]
In this #expertseries, Rahul Vijayan from Red Hat is sharing about RHEL at the Edge.

This blog shows how to use RHACM GitOps to install Service Mesh and configure the default control plan. If your […]
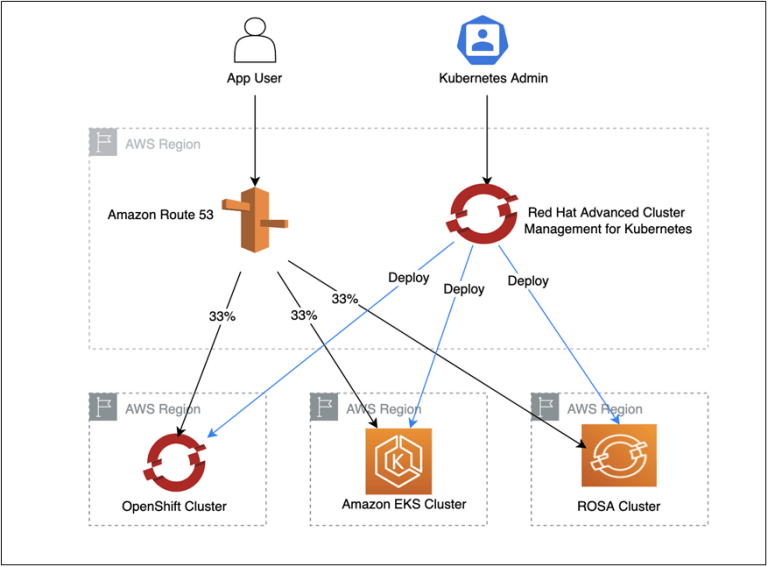
This blog shows how to prepare RHACM and manage the cluster on AWS. Installing Red Hat Advanced Cluster Management Using OperatorHub, […]

Nearly 35 speakers are already lined up for the tech talks, refer to the event schedule for more details about […]