
Connecting Ansible Tower to Git Server with Self Signed Certificates
So many questioned me when I mention git server in an Ansible Tower environment; and later I realized that, most of them are keeping their projects inside Ansible Tower !!!

Okay, that is just an option in Ansible Tower and Highly NOT Recommended for production setup or for environment with multiple teams accessing the Ansible Tower.
Why Should Not ?
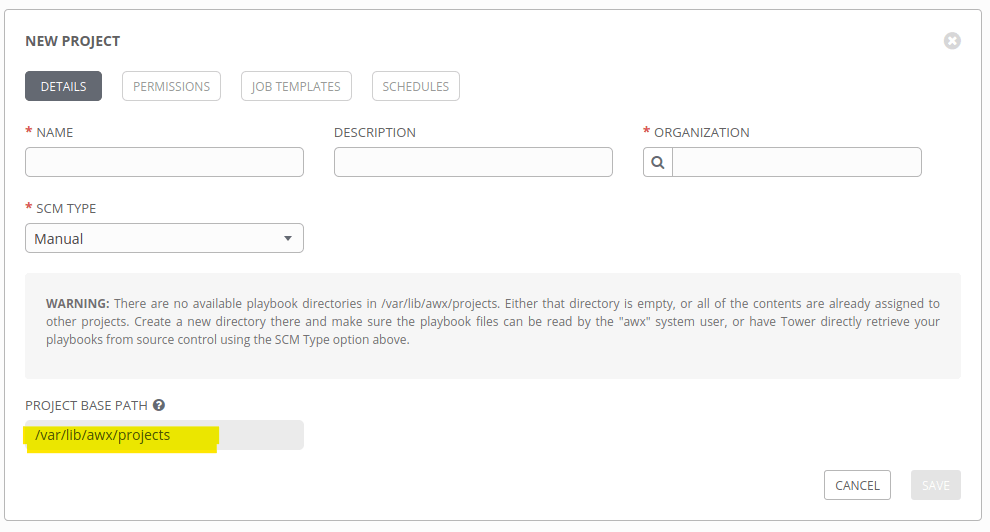
- You need to give permission for each and every user to this Ansible Tower node and to this directory –
/var/lib/awx/projects - It won’t be effective when you deploy Ansible Tower as multi-node cluster as you need to update the playbooks and project files in every node, under
/var/lib/awx/projects - Less control on editing playbooks or files as you have to do everything from CLI (mostly Ansible Tower nodes installs on nodes without GUI)
- Other users can easily access other projects and files if you didn’t configure your directory properly.
- and many other reasons…
Also Read : How to Add Custom modules in Ansible
Ansible Tower supports most of the common SCM (Source Control Management) technologies as you can see below and yes, the easiest and simple one is using a Git server.
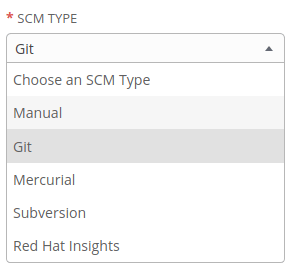
It can be GitHub, GitLab, BitBucket etc but most of the time, enterprise environments will be in a disconnected network – without internet access – and accessing those services will not work. So what, we have so many FREE/OpenSource/Enterprise git server alternatives like GiLab, BitBucket, Gogs etc and we can deploy this in our environment and keep our Ansible playbooks and project files there.
Read : How to install Git Server using Gogs
So, you have deployed a local git server using Gogs or GitLab CE/EE and connected project repos from there.
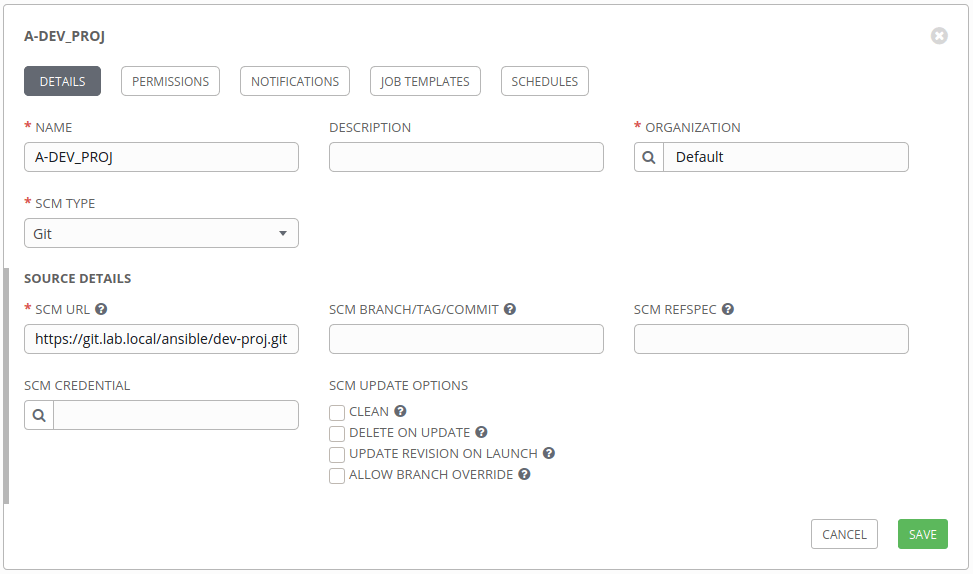
And you found the there is an error to connect to the git server from Ansible Tower !
{
"stderr_lines": [
"fatal: unable to access 'https://$encrypted$:$encrypted$@https://git.lab.local/ansible/dev-proj.git/': Peer's certificate issuer has been marked as not trusted by the user."
],
.
.
.
<truncated...>
.
.
"stderr": "fatal: unable to access 'https://$encrypted$:$encrypted$@https://git.lab.local/ansible/dev-proj.git/': Peer's certificate issuer has been marked as not trusted by the user.\n",
.
.
<truncated...>
.
.
"msg": "fatal: unable to access 'https://$encrypted$:$encrypted$@https://git.lab.local/ansible/dev-proj.git/': Peer's certificate issuer has been marked as not trusted by the user."
}And yes, most of the organizations will not spend money for CA/SSL Certificates and use self-signed certificates instead; even for Ansible Tower. And sometimes, even with CA Certificate, Ansible tower may not able to validate the Certificate.
And in our case, Ansible Tower cannot verify the certificate authority and shows Peer's certificate issuer has been marked as not trusted by the user Error. So, what is next ?
The Solution
Actually this is very simple, you can easily configure the same in Ansible Tower as EXTRA ENVIRONMENT VARIABLES.
Option 1 – Ignore SSL Verification
You can tell Ansible Tower to ignore the SSL verification as below.
{
"GIT_SSL_NO_VERIFY": "True"
}Option 2 – Provide Root Bundle Certificate
You can mention the root bundle Certificate from Certificate Authority
{
"GIT_SSL_CAINFO": "/etc/custom-ca/bundle-ca.crt",
}
Where Should I Do this ?
Inside Ansible Tower GUI, goto Settings -> Job, and find the EXTRA ENVIRONMENT VARIABLES. Add variable in JSON format and Save it.

Test your project by syncing again and that’s it.
Disclaimer:
The views expressed and the content shared in all published articles on this website are solely those of the respective authors, and they do not necessarily reflect the views of the author’s employer or the techbeatly platform. We strive to ensure the accuracy and validity of the content published on our website. However, we cannot guarantee the absolute correctness or completeness of the information provided. It is the responsibility of the readers and users of this website to verify the accuracy and appropriateness of any information or opinions expressed within the articles. If you come across any content that you believe to be incorrect or invalid, please contact us immediately so that we can address the issue promptly.
Tags:
Comments
9 Responses
Leave a Reply






For defining the ca authority, where would that be uploaded or added for a local ca?
If you are using custom CA or ICA, then you can add the CA certificate on the Ansible Tower machine.
Read: How to install a CA certificate on Red Hat Enterprise Linux 7 and later (https://access.redhat.com/solutions/5868401)
Hi Gineesh, Thanks a lot for your informative solution,
In ansible automation platform everything runs by containers so we need an extra step for customizing the controller container image and adding the required CA-Bundle to the path in that image.
Best Regards
You are right. AAP2 onwards several things changed and you need to take care of containerizing most of the items including collections and other details for your projects.
I am having a similar problem with an internal Automation Hub I deployed. When I try to sync a job and pull in the playbook requirements I get a failure because of a self-signed certificate in the chain. That certificate is an internal CA and I did install that CA on the system but is seems as though the system CA store is not checked.
I guess I need to set a different environment variable for the Ansible Repository so I will do a search on what variables are available. Thanks for the article though – given me a path forward.
If AWX GUI doesn’t have edit form option to add in extra environment variables, how can we do this verify ssl as false via CLI
AWX without GUI? Could you please explain?
or chat here: t.me/techbeatly
Unable to edit form for job settings in open source. What’s the alternate option to add ssl verify false while creating project
Which version of Ansible AWX are you using?